Custom Privacy OS Comparison
GrapheneOS / DivestOS / CalyxOS / IodeOS / eOS / LineageOS
UPDATED: 28 October 2025Facts Review Rather Than Marketing
Rather than sharing my technical opinion on how Graphene OS running on a Pixel phone is better than any of the other custom privacy / security operating systems [DivestOS / CalyxOS / IodeOS / eOS / LineageOS / AOSP] I thought it better to present the facts and let you decide yourself — David
We also sell DeGoogle Phones and Secure Phones with Graphene OS and express post Australia Wide.
Comparison of Custom Privacy Operating Systems
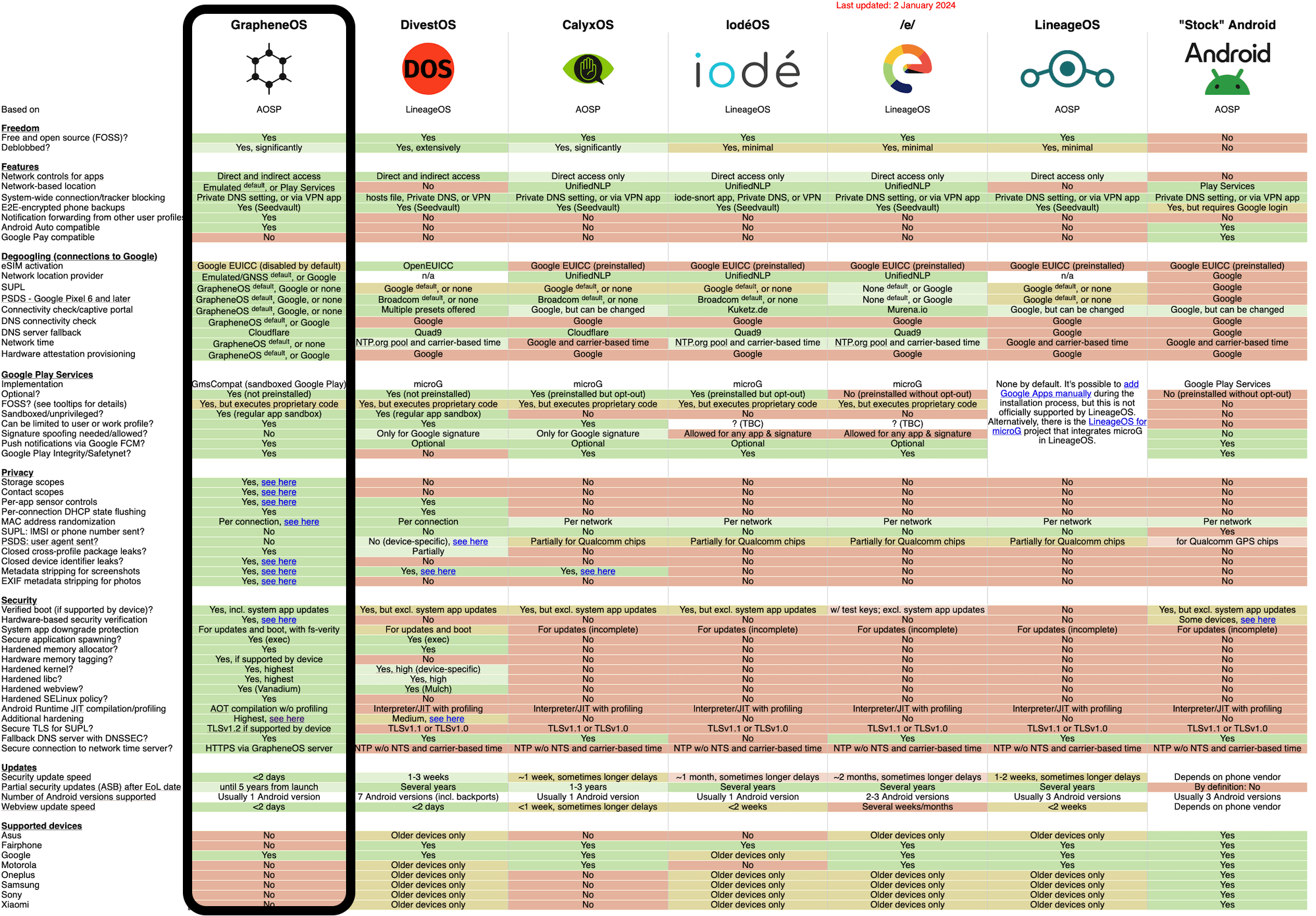
Below is a factual, features based comparison between the majority of alternate mobile operating systems, often portrayed as improved privacy and/or security. In reality, their marketing often outperforms their OS, be it intentional or not, giving people a false confidence in the OS. This I find concerning. Just a cursory glance at the comparison chart below, quickly informs the viewer of the significant differences between Graphene OS and the other Operating Systems. I support Graphene Pixel phones because they provide the best privacy and security! I assume that’s why Ed Snowden does too.
Summary
If you really want a private [spy free] phone in 2025, in all good faith, I can only recommend the Pixel 8 / 9 / 10 Series phones running Graphene OS. For those who require the very best privacy AND security [spy free and serious hacking protection] then the Pixel 9 and 10 Series with Graphene OS have the latest advance [extreme] security. Keep reading for the full details — David
The Android Operating System
When you buy a modern mobile phone [be it Android or iPhone] the device’s default operating system includes invasive integration with apps and services, which is a technical way of saying "it’s spying on you". If you buy an Android phone [basically anything other than an iPhone] a perfect example of the invasive apps and/or services, would be the Google Play Services. The Google Play Services have irrevocable privileges to access your files, contacts storage, call logs, SMS messages, location, camera, microphone, hardware identifiers, and so on. These apps and services increase the attack surface of your device [places where hackers can attempt entry] and are also the source of considerable privacy concerns with Android OS phones, and in fact, all mobile phones.
This problem can be solved by using a custom Android-based operating system that does not come with such invasive integration and spying. Unfortunately, basically all custom Android based operating systems violate the Android security model by not supporting critical security features such as AVB, rollback protection, firmware updates, and so on. Some of them also ship "userdebug" builds which expose root over ADB, and require more permissive "SELinux" policies to accommodate debugging features, resulting in a further increased attack surface and weakened security model. These are serious issues, not well understood by the average user choosing a custom OS. When choosing a custom operating system, you should make sure that it upholds the Android security model, again Graphene OS leads the way.
Baseline Security
Verified Boot
Verified Boot is an important part of the Android security model. It provides protection against evil maid attacks, malware persistence, and ensures security updates cannot be downgraded with rollback protection. On Android, only your data (inside of the /data partition) is encrypted, and the operating system files are left unencrypted. Verified Boot ensures the integrity of the operating system files, thereby preventing an adversary with physical access from tampering or installing malware on the device. In the unlikely case that malware is able to exploit other parts of the system, and gain higher privileged access, Verified Boot will prevent and revert changes to the system partition upon rebooting the device. This is a significant advantage that is offered on the Graphene Pixel phones! Unfortunately, most phone manufactures do not support Verified Boot, and those that do, only support it with their original [spying] OS. Once you install a custom OS, the Verified Boot is no longer effective.
Firmware Updates
Firmware [hardware component management software] updates are critical for maintaining security and without them your device cannot be secure. Phone manufactures have support agreements with their partners to provide the closed-source components for a limited support period. On a custom Android OS, it is the responsibility of the OS vendor to extract the firmware from the stock operating system, test it against their Android builds, then ship them to the user. Unfortunately, many custom OS distributions, including extremely popular ones like Lineage OS and eOS do not ship firmware updates for most of their supported device. Instead, they expect the user to keep track of stock OS updates, extract and flash the firmware themselves. Beyond the lack of testing, this is extremely burdensome and not feasible for most end users and is yet another reason to not use these distributions.
Patch Levels
As the Official Android OS [AOSP] issues its Security Updated every month, Android-Based operating systems are expected to apply all security fixes before the next Security Update comes out. Beside extracting the firmware, testing it and shipping it to the end user as described above, the AOSP based system also needs to be updated. This is a particularly challenging thing to do, especially around the time of a new major Android release since there are a lot of changes. Sometimes, newer firmware versions require newer major versions of AOSP, and if the developer takes too long to update their base operating system to the next major AOSP version, they cannot ship firmware updates either, leaving users vulnerable. This actually occurred with Calyx OS during the Android 11 to Android 12 transition. It took them 4 months to update to Android 12 and during those 4 months, they could not ship any firmware updates at all, leaving the user vulnerable during that time period.
Webview Updates
Android comes with a system webview, a component that many apps rely on to use as part of their activity layout. It effectively behaves like a minimal browser, opening random websites with arbitrary code. It is very important that this component is consistently kept up to date and secure. Some custom Android operating systems, such as Calyx OS, often fall behind on security updates for this component. Particularly, this has gotten so bad that they actually fell behind for 3 months back in January 2022 and 2 months in June 2022. It is a good indication that these operating systems cannot keep up with security updates and should not be used.
User Builds
As mentioned above, "userdebug" builds expose root over ADB and require more permissive "SELinux" policies to accommodate debugging features. They violate the Android security model and are really only meant for developers to test out their android builds during development. End users should be using the production user builds. Custom OS distributions which do not ship user builds like Lineage OS or eOS should be avoided, especially if your device has not reached end of life.
SELinux in Enforcing Mode
"SELinux" is a critical part of the Android security model, having the Linux kernel enforcing confinement for all processes, including system processes running as root. In order for a system to be secure, it must have SELinux in Enforcing mode, accompanied by fine-grained SELinux policies. Once again, many custom Android OS builds [especially unofficial LineageOS builds] disable SELinux or set it into Permissive mode. You can check whether SELinux is in enforcing mode or not by executing "getenforce" in the ADB shell [the expected output is Enforcing]. You should avoid any custom Android OS builds that do not have SELinux in enforcing mode at all cost.